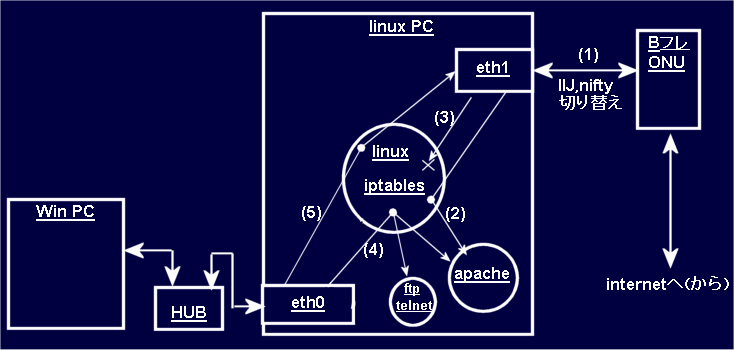
#!/bin/sh
#iptablesコマンド使った firewallの設定スクリプト
LOCAL_NET='192.168.0.0/16'
CLIENT_A='192.168.0.2'
#基本ポリシー (-Pオプション)の設定
#INPUTは拒否 DROP
#OUTPUTは許可 ACCEPT
#FORWARDは拒否 DROP
#
iptables -P INPUT DROP
iptables -P OUTPUT ACCEPT (DROPが基本というサイトが大多数です、念のため)
iptables -P FORWARD DROP
#個別ルールを全削除
#
iptables -F
iptables -t nat -F
#ユーザー定義チェインを削除
#
iptables -X
#ループバックに関してはすべて許可
#
iptables -A INPUT -s 127.0.0.1 -d 127.0.0.1 -j ACCEPT
#自分が発するコマンドを許可
#
#iptables -A INPUT -i lo -j ACCEPT
#(この設定はセキュリティー上良くなかった?)
#(次の行の設定に変更しました)
iptables -A INPUT -s 192.168.0.25 -d 192.168.0.25 -j ACCEPT
#eth0から入ってくる LOCAL NET PCからの通信を許可
#
iptables -A INPUT -i eth0 -p all -s $LOCAL_NET -j ACCEPT
# 発信元が loop back private addressのパケットを拒否
#
iptables -A INPUT -i ppp0 -s 127.0.0.0/8 -j DROP
iptables -A INPUT -i ppp0 -s 10.0.0.0/8 -j DROP
iptables -A INPUT -i ppp0 -s 176.16.0.0/12 -j DROP
iptables -A INPUT -i ppp0 -s 192.168.0.0/16 -j DROP
# TCP PORT 80,8080の通過を許可
#
iptables -A INPUT -i ppp0 -p tcp --dport 80 -j ACCEPT
iptables -A INPUT -i ppp0 -p tcp --dport 8080 -j ACCEPT
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
# PORT 135 rpc
# 137 netbios
# 138 netbios
# 139 file/printer共有
# 445 file/printer共有
# ppp0へ向けて出て行く以上のパケットは DROP
#
iptables -A FORWARD -p udp -i eth0 -o ppp0 --dport 135:139 -j DROP
iptables -A FORWARD -p tcp -i eth0 -o ppp0 --dport 135:139 -j DROP
iptables -A FORWARD -p udp -i eth0 -o ppp0 --dport 445 -j DROP
iptables -A FORWARD -p tcp -i eth0 -o ppp0 --dport 445 -j DROP
# 送信先が LOCAL ADDRESSの物が ppp0へ向けて出て行ったら DROP
#
iptables -A FORWARD -o ppp0 -d 192.168.0.0/16 -j DROP
#eth0からeth1へ向けてのパケットは許可
#
iptables -A FORWARD -i eth0 -o ppp0 -s $LOCAL_NET -j ACCEPT
iptables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT
# LANから外に出て行くパケットの送信元IPを書き換え
#
iptables -t nat -A POSTROUTING -o ppp0 -s $LOCAL_NET -j MASQUERADE
# ループバック宛、プライベートアドレス宛のパケットが漏れるのを防ぐ
#
iptables -A OUTPUT -o ppp0 -d 127.0.0.0/8 -j DROP
iptables -A OUTPUT -o ppp0 -d 10.0.0.0/8 -j DROP
iptables -A OUTPUT -o ppp0 -d 176.16.0.0/12 -j DROP
iptables -A OUTPUT -o ppp0 -d 192.168.0.0/16 -j DROP
# NetBIOS over TCP/IP の流出パケットを遮断
#
iptables -A OUTPUT -o ppp0 -p tcp --dport 135:139 -j DROP
iptables -A OUTPUT -o ppp0 -p udp --dport 135:139 -j DROP
iptables -A OUTPUT -o ppp0 -p tcp --dport 445 -j DROP
iptables -A OUTPUT -o ppp0 -p udp --dport 445 -j DROP
|